14期学员,想请教一下如何判断应用闪退的思路,目前使用的框架是uiautomator2
目前自己想到的方法是监控logcat,当有ANR或者Fatal时就执行后续的代码,如下图
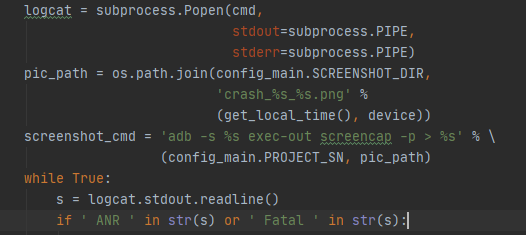
现在有如下疑问
1.有些闪退logcat中打印的不是anr或者fatal,那么这种应该如何判断呢
这里自动化工具检测不到元素报错是一种方法,但是这种需要去排查是什么原因导致找不到元素,我是想知道有没有其它更好的方法,可以直接定位到闪退
2.如果 android系统或者其它系统 有自身或者不是被 测APP的CRASH log被读取到,那么这种应该如何避免呢?
bugly这种是没有的 目前主要测试的是手机内置的APP,和整个系统的测试
堆栈的字符串是不是需要向开发询问呢?
- 手机内置的APP我觉得无论什么时候都考虑接入崩溃平台,这个作为APP的基础建设
- 堆栈字符串这种不需要和开发询问啊;你要自己写代码去判断堆栈字符串的啊;
举个例子:
正常输出
07-20 17:16:50.986 1014 1356 E WifiVendorHal: getWifiLinkLayerStats(l.937) failed {.code = ERROR_NOT_SUPPORTED, .description = }
07-20 17:16:51.629 1014 1014 I DeviceIdleController: updateChargingLocked: charging=true
07-20 17:16:51.629 1014 1014 I DeviceIdleController: becomeActiveLocked, reason = charging
07-20 17:16:51.638 4284 4284 I PC_BatteryChangedRcv: level: 51, remindValue: 15, status: 2
07-20 17:16:51.639 4284 4284 D PC_BatteryChangedRcv: isGameMode: false
07-20 17:16:51.639 4284 4284 D PC_BatteryChangedRcv: onReceive: false
07-20 17:16:51.639 4284 4284 D PC_BatteryChangedRcv: isGameMode: false
07-20 17:16:51.640 4284 4284 D PC_NotificationUtils: cancelNotification:
07-20 17:16:51.640 4284 4284 D PC_BatteryChangedRcv: onReceive: battary on charge
堆栈异常
07-20 17:16:50.239 4093 7518 E Auth : [GoogleAccountDataServiceImpl] getToken() -> NETWORK_ERROR. Account: <ELLIDED:949424707>, App: com.google.android.gms, Service: oauth2:https://www.googleapis.com/auth/webhistory
07-20 17:16:50.239 4093 7518 E Auth : pip: Error when calling server.
07-20 17:16:50.239 4093 7518 E Auth : at gby.a(:com.google.android.gms@202414063@20.24.14 (110306-319035315):113)
07-20 17:16:50.239 4093 7518 E Auth : at gah.a(:com.google.android.gms@202414063@20.24.14 (110306-319035315):124)
07-20 17:16:50.239 4093 7518 E Auth : at csb.a(:com.google.android.gms@202414063@20.24.14 (110306-319035315):238)
07-20 17:16:50.239 4093 7518 E Auth : at csb.a(:com.google.android.gms@202414063@20.24.14 (110306-319035315):111)
07-20 17:16:50.239 4093 7518 E Auth : at csb.a(:com.google.android.gms@202414063@20.24.14 (110306-319035315):246)
07-20 17:16:50.239 4093 7518 E Auth : at cqb.onTransact(:com.google.android.gms@202414063@20.24.14 (110306-319035315):5)
07-20 17:16:50.239 4093 7518 E Auth : at android.os.Binder.transact(Binder.java:667)
07-20 17:16:50.239 4093 7518 E Auth : at ctw.onTransact(:com.google.android.gms@202414063@20.24.14 (110306-319035315):2)
07-20 17:16:50.239 4093 7518 E Auth : at android.os.Binder.transact(Binder.java:667)
07-20 17:16:50.239 4093 7518 E Auth : at xtb.onTransact(:com.google.android.gms@202414063@20.24.14 (110306-319035315):17)
07-20 17:16:50.239 4093 7518 E Auth : at android.os.Binder.execTransact(Binder.java:731)
07-20 17:16:50.239 4093 7518 E Auth : Caused by: javax.net.ssl.SSLHandshakeException: SSL handshake aborted: ssl=0xa2fdadb8: I/O error during system call, Connection reset by peer
07-20 17:16:50.239 4093 7518 E Auth : at com.google.android.gms.org.conscrypt.NativeCrypto.SSL_do_handshake(Native Method)
07-20 17:16:50.239 4093 7518 E Auth : at com.google.android.gms.org.conscrypt.NativeSsl.doHandshake(:com.google.android.gms@202414063@20.24.14 (110306-319035315):6)
07-20 17:16:50.239 4093 7518 E Auth : at com.google.android.gms.org.conscrypt.ConscryptFileDescriptorSocket.startHandshake(:com.google.android.gms@202414063@20.24.14 (110306-319035315):16)
07-20 17:16:50.239 4093 7518 E Auth : at amms.a(:com.google.android.gms@202414063@20.24.14 (110306-319035315):22)
07-20 17:16:50.239 4093 7518 E Auth : at amms.createSocket(:com.google.android.gms@202414063@20.24.14 (110306-319035315):9)
07-20 17:16:50.239 4093 7518 E Auth : at com.android.okhttp.internal.io.RealConnection.connectTls(RealConnection.java:181)
07-20 17:16:50.239 4093 7518 E Auth : at com.android.okhttp.internal.io.RealConnection.connectSocket(RealConnection.java:149)
07-20 17:16:50.239 4093 7518 E Auth : at com.android.okhttp.internal.io.RealConnection.connect(RealConnection.java:112)
07-20 17:16:50.239 4093 7518 E Auth : at com.android.okhttp.internal.http.StreamAllocation.findConnection(StreamAllocation.java:184)
07-20 17:16:50.239 4093 7518 E Auth : at com.android.okhttp.internal.http.StreamAllocation.findHealthyConnection(StreamAllocation.java:126)
07-20 17:16:50.239 4093 7518 E Auth : at com.android.okhttp.internal.http.StreamAllocation.newStream(StreamAllocation.java:95)
07-20 17:16:50.239 4093 7518 E Auth : at com.android.okhttp.internal.http.HttpEngine.connect(HttpEngine.java:299)
07-20 17:16:50.239 4093 7518 E Auth : at com.android.okhttp.internal.http.HttpEngine.sendRequest(HttpEngine.java:237)
07-20 17:16:50.239 4093 7518 E Auth : at com.android.okhttp.internal.huc.HttpURLConnectionImpl.execute(HttpURLConnectionImpl.java:472)
07-20 17:16:50.239 4093 7518 E Auth : at com.android.okhttp.internal.huc.HttpURLConnectionImpl.connect(HttpURLConnectionImpl.java:127)
07-20 17:16:50.239 4093 7518 E Auth : at com.android.okhttp.internal.huc.HttpURLConnectionImpl.getOutputStream(HttpURLConnectionImpl.java:258)
07-20 17:16:50.239 4093 7518 E Auth : at com.android.okhttp.internal.huc.DelegatingHttpsURLConnection.getOutputStream(DelegatingHttpsURLConnection.java:218)
07-20 17:16:50.239 4093 7518 E Auth : at com.android.okhttp.internal.huc.HttpsURLConnectionImpl.getOutputStream(HttpsURLConnectionImpl.java:26)
07-20 17:16:50.239 4093 7518 E Auth : at zgg.a(:com.google.android.gms@202414063@20.24.14 (110306-319035315):26)
07-20 17:16:50.239 4093 7518 E Auth : at iyi.a(:com.google.android.gms@202414063@20.24.14 (110306-319035315):5)
07-20 17:16:50.239 4093 7518 E Auth : at gbk.a(:com.google.android.gms@202414063@20.24.14 (110306-319035315):9)
07-20 17:16:50.239 4093 7518 E Auth : at gbk.a(:com.google.android.gms@202414063@20.24.14 (110306-319035315):5)
07-20 17:16:50.239 4093 7518 E Auth : at gby.a(:com.google.android.gms@202414063@20.24.14 (110306-319035315):112)
07-20 17:16:50.239 4093 7518 E Auth : ... 10 more
怎么能判断他是正常输出还是堆栈输出这个就要看你的编程思维了!!!
ps:可以略微提一句:就是tag也是一个很常用的判断方式,比如有异常的tag都是e(error),但是也不一定



